The Java applet attack is one of the most successful attack vectors in SET and has the highest success rate for compromise system. Popular because we can create the infected Java applet very easily,we can clone any site we want that will load the applet very fast and successful because it affects all the platforms.The only difficulty is how to deliver the Java Applet properly in order to trick our victims.
The Java Applet attack will create a malicious Java Applet that once run, will completely compromise the victim. The neat trick with SET is that you can completely clone a website and once the victim has clicked run, it will redirect the victim back to the original site making the attack much more believable.
The Java applet Attack vector affects:
Windows Systems
Linux Systems and
Mac OS X
We are opening the Social Engineering Toolkit and we choose the option Website Attack Vector.
you need to select 2 and then press enter:
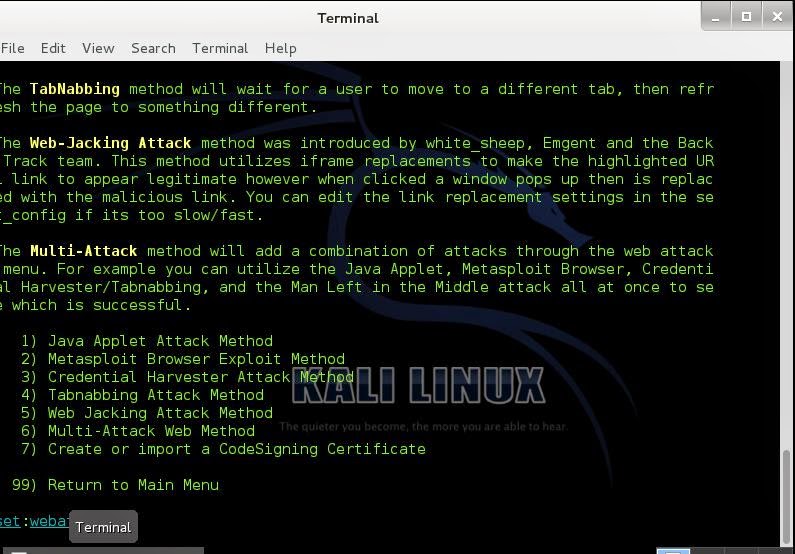
In the next menu we will choose the first option the Java Applet Attack Method:
In the next section, we will see there are three options:
The option site cloner would be used in order to recreate the website of our choice that will carry the malicious Java applet.
Now in the next menu, it will ask are you using NAT ?
Set yes if you use !
Enter the URL of your choice and click enter. Here i am using www.hacxorprogramming.blogspot.in but you can use any website you feel comfortable that can trick the users to run the Java Applet.
The next part is to decide which payload it will be used.There is a variety of available payloads that SET provides but here we have chosen to use a simple Windows Shell Reverse TCP :
You have now succesfully cloned a website, but you're not done. Now you need to bypass anti virus software for this to actually work. we have chosen the Backdoored Executable which is the best choice there:
The next option has to do with the port of the listener.You can press enter in order the SET to choose the default port which is 443.
Our next step now is to try to find a way to mask our IP address in order to have a domain that will look original.We can register a domain or we can use any of the online shorten URL services to hide our IP when we will send the link to our target.
Note : If you had changed the configuration file to include WEBATTACK_EMAIL=ON, you
would have been prompted to send an email using the spear-phishing attack vector
(minus attachments).
Now that everything is set up, you simply need to get a target to browse to the malicious site. Upon reaching the website, the target sees a pop-up warning from the publisher. If the target clicks Run, and most users will, the payload will be executed, and you gain full control of the user’s system.
Now it’s up to you to convince your victim to click on the link but once they do they will be brought to your cloned website and an “accept certificate” window will pop up. If they click on it and Back at our attacker machine, the Meterpreter session is successfully established,
The Java Applet attack will create a malicious Java Applet that once run, will completely compromise the victim. The neat trick with SET is that you can completely clone a website and once the victim has clicked run, it will redirect the victim back to the original site making the attack much more believable.
The Java applet Attack vector affects:
Windows Systems
Linux Systems and
Mac OS X
We are opening the Social Engineering Toolkit and we choose the option Website Attack Vector.
you need to select 2 and then press enter:
In the next menu we will choose the first option the Java Applet Attack Method:
In the next section, we will see there are three options:
The option site cloner would be used in order to recreate the website of our choice that will carry the malicious Java applet.
Now in the next menu, it will ask are you using NAT ?
Set yes if you use !
Enter the URL of your choice and click enter. Here i am using www.hacxorprogramming.blogspot.in but you can use any website you feel comfortable that can trick the users to run the Java Applet.
The next part is to decide which payload it will be used.There is a variety of available payloads that SET provides but here we have chosen to use a simple Windows Shell Reverse TCP :
You have now succesfully cloned a website, but you're not done. Now you need to bypass anti virus software for this to actually work. we have chosen the Backdoored Executable which is the best choice there:
The next option has to do with the port of the listener.You can press enter in order the SET to choose the default port which is 443.
Our next step now is to try to find a way to mask our IP address in order to have a domain that will look original.We can register a domain or we can use any of the online shorten URL services to hide our IP when we will send the link to our target.
Note : If you had changed the configuration file to include WEBATTACK_EMAIL=ON, you
would have been prompted to send an email using the spear-phishing attack vector
(minus attachments).
Now that everything is set up, you simply need to get a target to browse to the malicious site. Upon reaching the website, the target sees a pop-up warning from the publisher. If the target clicks Run, and most users will, the payload will be executed, and you gain full control of the user’s system.
Now it’s up to you to convince your victim to click on the link but once they do they will be brought to your cloned website and an “accept certificate” window will pop up. If they click on it and Back at our attacker machine, the Meterpreter session is successfully established,





No comments:
Post a Comment