Metasploit is the most advanced and popular Framework that can be used
for pen-testing.
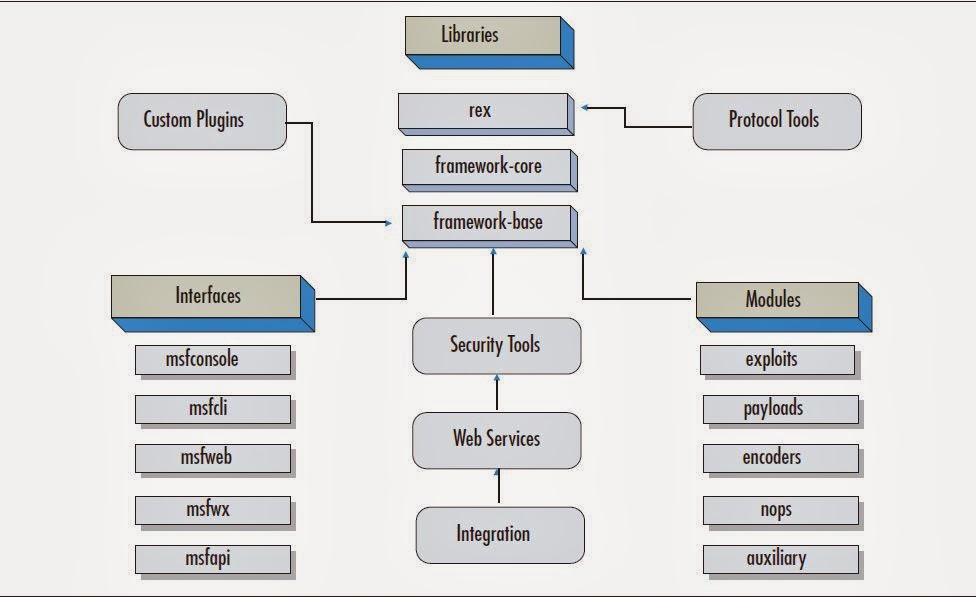
Metasploit Framework :
From the above pic,
You can see the main components of the framework architecture are:
Rex
Framework Core
Framework Base
Interfaces
Modules
Plugins
Framework Core
Framework Base
Interfaces
Modules
Plugins
Interfaces : -
Metasploit offers more than one interface to its underlying
functionality, including console, command line, and graphical
interfaces.
MSFconsole :
Msfconsole is by far the most popular part of the Metasploit Framework
Starting MSFconsole
To launch msfconsole, enter msfconsole at the command line.
Tab Completion :
Tab completion depends on the ruby readline extension and nearly every
command in the console supports tab completion.
use exploit/windows/dce
use .*netapi.*
set LHOST
show
set TARGET
set PAYLOAD windows/shell/
exp
use .*netapi.*
set LHOST
show
set TARGET
set PAYLOAD windows/shell/
exp
MSFcli :
Msfcli and msfconsole take very different approaches to providing
access to the Framework.
msfcli runs directly from the command line, which allows you to
redirect output from other tools into msfcli and direct msfcli output
to other command-line tools.
Benefits of mscli :
Supports the launching of exploits and auxiliary modules
Convenient to use when testing or developing a new exploit
Good tool for one-off exploitation
Excellent if you know exactly which exploit and options you need
Wonderful for use in scripts and basic automation
Convenient to use when testing or developing a new exploit
Good tool for one-off exploitation
Excellent if you know exactly which exploit and options you need
Wonderful for use in scripts and basic automation
Armitage :
The armitage component of Metasploit is a fully interactive graphical
user interface.
Running Armitage
To launch armitage, run the command armitage.
After armitage is running, simply click a menu to perform a particular
attack or access other Metasploit functionality
Metasploit Utilities:
MSFpayload:
The msfpayload component of Metasploit allows you to generate shellcode,
executables, and much more for use in exploits outside of the Framework.
Shellcode can be generated in many formats including C, Ruby,
JavaScript, and even Visual Basic for Applications.
MSFencode:
The shellcode generated by msfpayload is fully functional, but it
contains several null characters that, when interpreted by many
programs, signify the end of a string, and this will cause the code to
terminate before completion.
In other words, those x00s and xffs can break your payload!
To avoid detection ,Metasploit’s developers offer msfencode, which
helps you to avoid bad characters and evade antivirus and IDSs by
encoding the original payload in a way that does not include “bad”
characters. Enter msfencode -h to see a list of msfencode options.
Exploits:
An exploit is the means by which an attacker, or pen tester for that
matter, takes advantage of a flaw within a system, an application, or a
service. An attacker uses an exploit to attack a system in a way that
results in a particular desired outcome that the developer never
intended.
All exploits in the Metasploit Framework will fall into two categories:
active and passive.
Active Exploits
Active exploits will exploit a specific host, run until completion, and
then exit.
Brute-force modules will exit when a shell opens from the victim.
Module execution stops if an error is encountered.
You can force an active module to the background by passing '-j' to
the exploit command.
Passive Exploits
Passive exploits wait for incoming hosts and exploit them as they
connect.
Passive exploits almost always focus on clients such as web browsers,
FTP clients, etc.
They can also be used in conjunction with email exploits, waiting for
connections.
Passive exploits report shells as they happen can be enumerated by
passing '-l' to the sessions command. Passing '-i' will interact with a shell.
Payloads :
A payload is code that we want the system to execute and that is to be
selected and delivered by the Framework
There are three different types of payload module types in Metasploit:
Singles, Stagers, and Stages.
Databases :
When conducting a penetration test, it is frequently a challenge to
keep track of everything you have done to the target network. This is
where having a database configured can be a great time saver. Metasploit
has built-in support for the PostgreSQL database system.
No comments:
Post a Comment