In this tutorial I will show you how to hack Facebook password with tab nabbing using SET.
Tab nabbing is a computer based exploit or it is also called Phishing attack. The attack takes advantage of user trust and inattention to detail in regard to tabs, and the ability of modern web pages to rewrite tabs and their contents a long time after the page is loaded. In a tabnabbing scenario, a target is caught while accessing a website with multiple tabs open. When the target clicks a link, he is presented with a “Please wait while the page loads” message. When the target switches tabs, the website detects that a different
tab has focus and rewrites the web page that presented the “Please wait . . . ” message with a website you specify. Eventually, the target clicks the tabnabbed tab, and, believing he is being asked to sign in to his email program or business application, he enters his credentials into the malicious look-alike site. The credentials are harvested, and the target is redirected to the original website. Tab nabbing operates in reverse of most phishing attacks in that it doesn’t ask users to click on an obfuscated link but instead loads a fake page in one of the open tabs in your browse
First thing we have to do of course is to open the Social Engineering Toolkit and to choose the Website Attack Vectors option :
Next we will see the available attacks that we can use.Of course our choice here is option number 4 and the Tab nabbing Attack Method
Now it is time to choose the website that the SET will clone.In this scenario our choice will be the Facebook.
If we send a link with our IP address to our victim and he opens it he will notice that a new tab will open and a message will
appear saying "Please wait while the page loads":
Note : You can also use tinyurl to hide the ip address of attacker…. Or there is also so many method available to request the victim to open the url..
Then after the Fake website will load and we just have to wait to enter his credentials in order to capture them.
The next image is showing what we will see in SET when the victim inserts his credentials into the username and password fields.
Watch Video Tutorial HERE.
Tab nabbing is a computer based exploit or it is also called Phishing attack. The attack takes advantage of user trust and inattention to detail in regard to tabs, and the ability of modern web pages to rewrite tabs and their contents a long time after the page is loaded. In a tabnabbing scenario, a target is caught while accessing a website with multiple tabs open. When the target clicks a link, he is presented with a “Please wait while the page loads” message. When the target switches tabs, the website detects that a different
tab has focus and rewrites the web page that presented the “Please wait . . . ” message with a website you specify. Eventually, the target clicks the tabnabbed tab, and, believing he is being asked to sign in to his email program or business application, he enters his credentials into the malicious look-alike site. The credentials are harvested, and the target is redirected to the original website. Tab nabbing operates in reverse of most phishing attacks in that it doesn’t ask users to click on an obfuscated link but instead loads a fake page in one of the open tabs in your browse
First thing we have to do of course is to open the Social Engineering Toolkit and to choose the Website Attack Vectors option :
Next we will see the available attacks that we can use.Of course our choice here is option number 4 and the Tab nabbing Attack Method
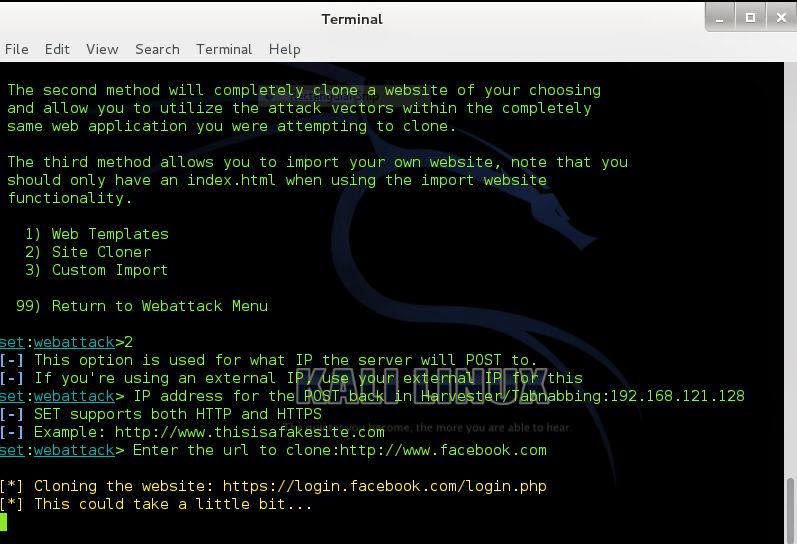
In the next menu we will choose option number 2 in order to clone the Website of our preference
Now enter your IP address
Now it is time to choose the website that the SET will clone.In this scenario our choice will be the Facebook.

If we send a link with our IP address to our victim and he opens it he will notice that a new tab will open and a message will
appear saying "Please wait while the page loads":
Note : You can also use tinyurl to hide the ip address of attacker…. Or there is also so many method available to request the victim to open the url..
Then after the Fake website will load and we just have to wait to enter his credentials in order to capture them.
The next image is showing what we will see in SET when the victim inserts his credentials into the username and password fields.
Watch Video Tutorial HERE.



